“These results also show the scope and the impact of LogoFAIL, since each IBV has at least one exploitable bug inside their parsers, and every parser contains bugs,” the Binarly researchers said in their technical write-up. “The only exception is Insyde’s PNG parser that is based on an open-source project and was likely already well-tested by the community. As we can see from the CWE column, we found a lot of different bug classes, from division-by-zero exceptions to NULL pointer dereference, from out-of-bounds reads to heap overflows.”
The Binarly team found these vulnerabilities through fuzz testing (fuzzing), which involves automatically generating malformed or unexpected input and feeding it to a target application to see how it behaves. If the application crashes, it usually means that a memory corruption occurred so the root cause is investigated to see if the corruption can be triggered and exploited in a controlled manner and therefore has security implications.
Fuzzing has become a standard process over the years and is now integrated into most code security testing tools that organizations use in the development stage, which is why the Binarly team was surprised to find so many exploitable crashes in the firmware. “The results from our fuzzing and subsequent bug triaging unequivocally say that none of these image parsers were ever tested by IBVs or OEMs,” the researchers concluded. “We can confidently say this because we found crashes in almost every parser we tested. Moreover, the fuzzer was able to find the first crashes after running just for a few seconds and, even worse, certain parsers were crashing on valid images found on the internet.”
Bypassing firmware security features
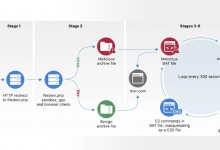
Planting malicious code early in a computer’s bootloader or in the BIOS/UEFI firmware itself is not a new technique. These programs have been referred to as boot-level rootkits, or bootkits, and offer huge advantages to attackers because their code executes before the operating system starts, allowing them to hide from any endpoint security products that might be installed inside the OS itself.
The low-level bootkit code usually injects malicious code into the OS kernel when it’s being loaded during the boot stage and that code then uses the kernel’s capabilities to hide itself from any user-installed programs, which is the typical definition of a rootkit — self-hiding malware that runs with root (kernel) privileges.
The modern UEFI firmware comes with several defenses against these attacks — if they’re enabled by the computer manufacturer. For example, UEFI Secure Boot is a feature that checks if the pieces of code loaded during the boot process have been cryptographically signed with a trusted key. This includes the firmware drivers, also known as Option ROMs, that are needed to initialize the various hardware components before the OS takes over, the EFI applications that run inside the firmware itself and the operating system bootloader and other components. Intel Boot Guard provides a hardware-based mechanism for establishing the cryptographic root of trust storing the OEM keys.