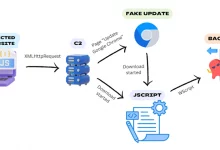
Here is what matters most when it comes to artificial intelligence (AI) in cybersecurity: Outcomes.
As the threat landscape evolves and generative AI is added to the toolsets available to defenders and attackers alike, evaluating the relative effectiveness of various AI-based security offerings is increasingly important — and difficult. Asking the right questions can help you spot solutions that deliver value and ROI, instead of just marketing hype. Questions like, “Can your predictive AI tools sufficiently block what’s new?” and, “What actually signals success in a cybersecurity platform powered by artificial intelligence?”
As BlackBerry’s AI and ML (machine learning) patent portfolio attests, BlackBerry is a leader in this space and has developed an exceptionally well-informed point of view on what works and why. Let’s explore this timely topic.
Evolution of AI in Cybersecurity
Some of the earliest uses of ML and AI in cybersecurity date back to the development of the CylancePROTECT® EPP (endpoint protection platform) more than a decade ago. Predicting and preventing new malware attacks is arguably more crucial today, as generative AI helps threat actors rapidly write and test new code. The most recent BlackBerry Global Threat Intelligence Report uncovered a 13% surge in novel malware attacks, quarter over quarter. Preventing these attacks is an ongoing challenge but thankfully, the evolution in attacks is being met by an evolution in technology.
BlackBerry’s data science and machine learning teams are dedicated to enhancing the performance of their predictive AI tools. Recent third-party tests confirm that Cylance ENDPOINT® successfully blocks 98.9% of threats by actively predicting malware behavior, even for new variants. This achievement is the result of a decade of innovation, experimentation, and evolution in AI techniques, including a shift from supervised human labeling to a composite training approach. This approach, which combines unsupervised, supervised, and active learning in both cloud and local environments, has been refined by analyzing extensive data over time, resulting in a highly effective model capable of accurately predicting and anticipating new threats.
Temporal Advantage: Taking Time Into Account
The quality and effectiveness of ML models are often discussed in terms of size, parameters, and performance. However, the critical aspect of ML models, particularly in cybersecurity, is their ability to detect and respond to threats in real-time. In the context of malware pre-execution protection, where threats must be identified and blocked before execution, the temporal aspect is crucial.
Temporal resilience, which measures a model’s performance against both past and future attacks, is essential for threat detection. Temporal Predictive Advantage (TPA) is a metric used to assess a model’s ability to perform over time, especially in detecting zero-day threats.
This testing involves training models with past malware classes and testing them against newer malware, validating their performance over time. This is particularly important for endpoints that are not always cloud-connected, where frequent model updates may not be feasible.
A model’s reliance on frequent updates can indicate its immaturity. In contrast, BlackBerry Cylance’s model has demonstrated a strong temporal predictive advantage, maintaining high detection rates without frequent model updates, as illustrated in the chart showing the TPA over months for the fourth-generation Cylance model.
| Chart 1 — The temporal predictive advantage for the fourth-generation Cylance AI model reveals how long into the future protection continues without a model update – in this case for six to 18 months. |
Protection continued for up to 18 months without a model update and reveals model maturity and precise model training. This does not happen by accident.
Mature AI Predicts and Prevents Future Evasive Threats has a novel ML model inference technology that sets it apart. It can deduce, or “infer” whether something is a threat, even when it has never seen it before. BlackBerry’s approach utilizes a unique hybrid method of distributed inference, a concept conceived seven years ago, before the availability of ML libraries and model-serving tools. The result of this approach is our latest model, which represents the pinnacle of innovation and improvements over the many generations of this technology.
Predicting Malware: The Most Mature Cylance Model
Built upon vast and diverse datasets with extensive malware behavior insights, our latest model surpasses all previous versions in performance, particularly in temporal predictive advantage. With over 500 million samples and billions of features evaluated, BlackBerry Cylance AI delivers outstanding results and operates with impressive speed for distributed inference.
As we continue to advance in applying ML to cybersecurity, our commitment to innovation remains strong. Given the increasing use of AI by adversaries, it’s essential to prioritize effective defensive cybersecurity measures that yield meaningful outcomes.
With a multi-year predictive advantage, Cylance AI has protected businesses and governments globally from cyberattacks since its inception. BlackBerry’s Cylance AI helps customers stop 36% more malware, 12x faster, and with 20x less overhead than the competition These outcomes demonstrate that not all AI is created the same. And not all AI is Cylance AI.
Want to learn more about predictive AI? Click here to read the detailed BlackBerry research article and explore related content and for similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
Related Reading
Note – This article has been expertly written by Shiladitya Sircar, SVP, Product Engineering & Data Science at BlackBerry, where he leads Cyber Security R&D teams.