Researchers warn that a cyberespionage actor that targets government entities in the Middle East and North Africa and is generally aligned with Palestinian interests has changed its infection chain tactics three times in recent months. The group is known for targeting a very small number of organizations in every campaign to deliver a custom malware implant dubbed IronWind.
Tracked as TA402 by security firm Proofpoint since 2020, the group’s attacks and techniques overlap with third-party reports attributing the activity to Molerats, Gaza Cybergang, Frankenstein, and WIRTE, so these might be different names for the same group.
“As of late October 2023, Proofpoint researchers had not observed any changes in targeting by TA402, an APT group that historically has operated in the interests of the Palestinian Territories, nor identified any indications of an altered mandate despite the current conflict in the region,” the Proofpoint researchers said in a new report. “It remains possible that this threat actor will redirect its resources as events continue to unfold.”
Malware delivered via Microsoft PowerPoint Add-ins, XLL and RAR attachments
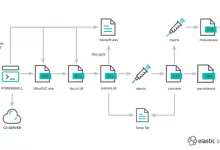
TA402 attacks start with spear-phishing emails sent from compromised email accounts of legitimate entities. In some of its recent campaigns, the group used an email account from a country’s Ministry of Foreign Affairs to send emails with a lure in Arabic that translates to “Economic cooperation program with the countries of the Gulf Cooperation Council 2023-2024.” The targets were other Middle Eastern government entities.
In previous campaigns observed during 2021 and 2022, the group’s phishing emails contained links that took users through a redirect script that checked their IP address location. Intended targets were served a RAR archive file that contained a malware program called NimbleMamba while those whose IP address location didn’t match the targeted area were redirected to a legitimate news site.
In new campaigns seen in July attackers included links in their emails that directed victims to download a malicious Microsoft PowerPoint add-in (PPAM) file from Dropbox. The following month the attackers changed their lure to “List of persons and entities (designated as terrorists) by the Anti-Money Laundering and Terrorist Financing Authority” and attached an XLL (Excel add-in) file directly to the email. In October the group shifted delivery tactics again and included malicious RAR attachments instead of XLL, while the lure was changed to “Report and Recommendations of the 110th Session on the War on Gaza.”