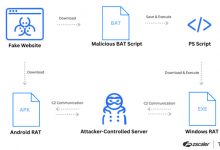
Some of the first phishing took place in the early 1990s when hackers used fake screen names to pose as AOL administrators and steal sensitive information via AOL Instant Messenger. Phishing really blew up in 2000, when an email with the subject line “ILOVEYOU” duped millions of people into clicking on an attachment loaded with a virulent computer worm.
In the early 2000s, hackers started impersonating sites such as PayPal by registering similar domain names for use in phishing emails. Circa the late 2000s, hackers began weaponizing personal information posted on social media sites, using it to make phishing emails seem more authentic. In the 2010s, bad actors began using malicious email attachments to spread ransomware like Cryptolocker and WannaCry.
Types of phishing attacks
Phishing has evolved into different formats and techniques over the past three decades.
Spear phishing targets one specific individual, often someone with access to an organization’s sensitive assets, such as an accountant or IT help desk employee. These emails usually contain personal information stolen from the dark web or gleaned from the target’s own social media posts.
A 2015 spear-phishing attack temporarily knocked out Ukraine’s power grid. Hackers targeted certain employees of the utility with emails containing malicious attachments; that malware gave the hackers access to the grid’s IT network.
BEC stands for business email compromise. The hacker impersonates a CEO or other top executive at a company, and then dupes an employee at that company into transferring corporate funds to a fake bank account. Sixty-eight percent of all phishing emails in 2022 were BEC attacks, according to SlashNext’s report. Per the FBI, global losses from BEC incidents reported between 2013 and 2022 totalled $50.8 billion.
Always keen to capitalize on current events, cyber crooks hijacked virtual meeting platforms during the pandemic, co-opting them for BEC attacks.
“Criminals … [are] compromising an employer or financial director’s email, such as a CEO or CFO, and requesting employees to participate in a virtual meeting platform,” the FBI warned in a 2022 alert.
“The criminal will insert a still picture of the CEO with no audio, or deep fake audio, and claim their video/audio is not properly working. They then proceed to instruct employees to initiate transfers of funds via the virtual meeting platform chat or in a follow-up email.”
An elaborate BEC hoax collectively cost Facebook and Google an eye-watering $100 million. Between 2013 and 2015, a scammer impersonated a board member from a real Taiwanese company. He sent phishing emails to Facebook and Google employees who regularly deal with large fund transactions, convincing them to ‘pay’ fake invoices to a fraudulent bank account.
Whale phishing targets a ‘big fish’ like a corporate CEO in order to steal a company’s funds, trade secrets or intellectual property.
Smishing is phishing via SMS text message. Thirty-nine percent of all mobile phishing attacks in 2022 involved smishing, according to the SlashNext report.
Quishing is phishing by QR code. The code is usually sent by email to dupe the target into downloading malware or visiting a fraudulent login page.
Vishing is phishing by phone call or voicemail. It often employs VoIP to thwart caller ID or wardialing to deliver thousands of automated voice messages.
Despite constant innovations in cybersecurity technology, some of the largest corporations on the planet have been fooled by low-tech phishing schemes. A vishing expedition shut down MGM Resorts (and its lucrative Las Vegas casinos) for more than a week in 2023.
Cybercriminals monitored an MGM employee’s LinkedIn account for personal details, then used that info to impersonate him in a phone call to MGM’s help desk. The hackers persuaded help desk staff to reset the employee’s password. Ransomware was deployed, guest data were stolen, and that sham phone call cost MGM $100 million.
AI and phishing
Hackers have added artificial intelligence to their phishing arsenal. Generative AI chatbots can quickly scrape millions of data points from the internet to craft phishing emails with no factual errors, convincingly mimicking the writing style of real individuals and organizations. Singapore’s cybersecurity agency reported that, in pen testing, phishing emails produced by ChatGPT “matched or exceeded the effectiveness” of those created by humans.
The number of phishing emails skyrocketed by 1,265 percent in the 12 months following ChatGPT’s general availability, prompting SlashNext CEO Patrick Harr to suggest it was “not a coincidence.”
Vishing scammers can harvest samples of people’s voices from social media video clips, and then clone their voices using generative AI. A Canadian grandma lost $7,000 (CDN) when fraudsters used AI to impersonate her grandson over the phone. AI vishing has even penetrated the C-suite. The CEO of a UK energy firm received three phone calls from the firm’s parent company, asking him to transfer $243,000 (USD) to a supplier. He dutifully sent the funds, but the voice was actually an AI replication.
How to prevent phishing
For individuals:
- If you think an email could be phishing, don’t reply, click on any links or attachments, or provide any sensitive information. Phone the organization or verify their email domain or URL by finding their website online.
- If an email requests a password or other sensitive information, or pressures you to take urgent action, pause and verify as noted above.
- Don’t post personal information on social media about your bank, birthdate, middle name, pets’ names or vacation plans.
For organizations:
- Ensure all software and applications are set to update and patch automatically.
- Implement multifactor authentication and strong password policies.
- Deploy tools such as Domain-based Message Authentication, Reporting and Conformance (DMARC), Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM).
- Regularly conduct pen testing.
- Continuously educate everyone in your organization about the latest phishing hazards using resources from organizations such as the SANS Institute.